Development of Scalable Linux Applications
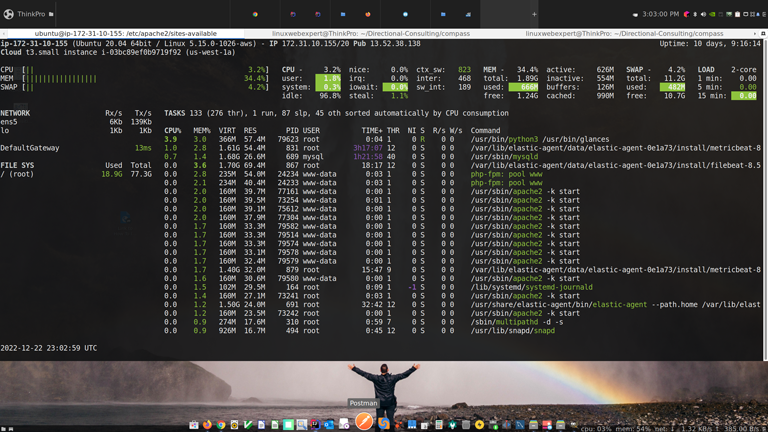
Real-time Process Monitoring
Our applications and system administration include process reliability, service layers monitoring, and fault-tolerant redundancy architecture. Knowing what resources each process and application consumes is critical to tuning a server and the connected applications for optimal real-time performance. We use tools that include history graphs, per-minute statistics, and deeper analysis with RRD graphs for providing monthly reports of uptime, average page access times, and application health metrics.
Enterprise Linux Security
Both flavors of Linux, RHEL, and Ubuntu have built-in Enterprise-grade security services. For example, SE Linux is available in the RedHat Enterprise Linux edition for built-in policy regulation of processes, protected system resources, and application disk access privileges. AppArmor is similar and available in the Ubuntu LTS Editions of Linux and performs equivalent tasks. We have extensive experience configuring safe access rules in both security applications using the policy managers.
OWASP CRS and Mod Security Protection
Every Directional Consulting deployment includes advanced security measures and auditing rules based on the open-source project OWASP ModSecurity Core Rule Set (CRS), a set of generic attack detection rules for use with ModSecurity or compatible web application firewalls. The CRS aims to protect web applications from a wide range of attacks, including the OWASP Top Ten, with a minimum of false alerts. In addition, the CRS covers many common attack categories, including:
- • SQL Injection (SQLi)
- • Cross-Site Scripting (XSS)
- • Local File Inclusion (LFI)
- • Remote File Inclusion (RFI)
- • PHP Code Injection
- • Java Code Injection
- • HTTPoxy
- • Shellshock
- • Unix/Windows Shell Injection
- • Session Fixation
- • Scripting/Scanner/Bot Detection
- • Metadata/Error Leakages
Detection of Intrusion and Hacking Attempts
Our standard deployment configuration includes additional security logs and enhanced detailed web server logs. In addition, our logging configuration captures remote countries, city locations, and remote IPs, which can block unwanted countries from accessing any resources just by country code. Finally, we design dashboards using Elastic Kibana and unique security log indexes to visualize system health and security threat levels.